Under the threat of ransomware, companies used to focus on processing and protecting data in servers and storage (SAN/NAS). However, company employees may not have enough awareness and resources on endpoint protection. Most senior officials in companies may still be under great threat to ransomware, which will kidnap their valuable and confidential data.
Ransomware is appearing more and more frequently in the public eye.
Let’s take a look at the truth that has happened before.
In 2017, WannaCry swept the world, and at least 150 countries and 30 million users were attacked, which had a huge impact on many industries such as finance, energy and medical care.
By 2021, security experts expect the global losses caused by ransomware attacks to reach $200 billion. This has increased 57fold in six years, confirming that ransomware is the fastest-growing type of cybercrime for consumers and businesses.


In March 2021, new active ransomware viruses were added around the world: Log4j, Hog, DearCry, Sarbloh, BadGopher, RunExeMemory, Phoenix CryptoLocker, etc. Among them, FancyBear is still in the development stage. DearCry is the first family to be captured this month to use Exchange vulnerabilities to send ransomware. The emerging PhoenixCryptoLocker may be related to Evil hacking organizations.
Ransomware has a wider range and harm to enterprises and individuals. This paper introduces some measures to prevent and deal with ransomware and focuses on endpoint protection, hoping to help readers avoid ransomware.
“Of course, you are never sure that criminals will keep their promises. It’s not a good idea to pay off when you are blackmailed by criminals. On the other hand, it is hard to blame them that enterprises that have lost the only copy of business-critical data may not help to take this risk.”
Is it cheaper to pay the ransom?
When an attack crosses all your prevention work and hijacks your network and data, it is easy for you to pay the ransom. When you compare the payment costs of employees who are unable to work and lose business due to future reputation damage during the downtime, the average ransom requirement paid seems to be economical. However, companies that pay ransoms do not receive decryption keys, and in many cases, companies are repeatedly attacked. So please don’t pay ransom to those lawbreakers. Let’s take a look at how Jetico helps us with endpoint protection
Endpoint protection is the battlefield where ransomware finally resists
Sincerely recommends Jetico endpoint protection from Ransomware as:

1) Jetico BestCrypt Data Shelter- Endpoint protection
protects folders from unwanted processes and users
Jetico released BestCrypt Data Shelter, a new cybersecurity tool that’s integrated with all Jetico encryption products. Designed to protect files and folders even when they’re in use, Data Shelter builds on the data-at-rest capabilities of BestCrypt products and provides customers with an additional layer of security. BestCrypt Data Shelter is also available independently as freeware.
Shelter Protection, – Jetico BestCrypt Data Shelter – “Free”
While files and folders on your PC can be protected in various ways, data in use remains vulnerable to attacks and prying eyes. Having that in mind, the development team at Jetico created the BestCrypt Data Shelter utility.
Well, it is a simple and user-friendly security tool that can protect data in use from getting stolen or intercepted. It practically creates a security shield to ensure your files and folders are secure and all the processes that are accessing the files are legit.
Working with BestCrypt Data Shelter is pretty easy, thanks to the user-friendly interface. The main window allows you to add new folders to protect and manage security policies. You can add as many directories as you need to protect and configure the policy for each.
Policies define authorized users and the processes that are allowed to make sure of the files inside the protected folder. You are free to select the users manually, set exceptions and then move on to programs.
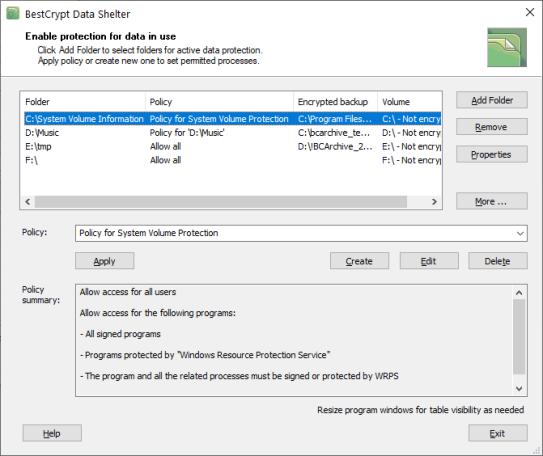
What is interesting about BestCrypt Data Shelter is that the application itself can help you create protection policies by studying the folder history. Moreover, it also works in conjunction with the “Windows Resource Protection”to make sure that files in a folder are only accessed by signed programs.
BestCrypt Data Shelter helps you get additional protection for your data, this time against malicious processes and unauthorized users. Custom security policies for individual folders offer you more control over your files. The idea is to ensure that data inside folders can only be accessed and used by active computers and trusted programs
BestCrypt Data Shelter provides protection against the rising number of cyberattacks by ensuring that folders on active computers can only be accessed by trusted programs and authorized users. The tool allows customers to create protection policies that are unique to selected folders, which helps to keep data safe and secure when it’s being used. Malware or ransomware may try to gain access to sensitive files by exploiting regular processes. Data Shelter can detect these harmful activities by monitoring communication between different processes – and keep your data safe from the storm.
Highlights of BestCrypt Data Shelter:
- Protect selected folders from unwanted programs and users
Create protection policies for any number of folders
Keep track of your encrypted drives and receive reminders about non-encrypted volumes
2) BestCrypt Volume Encryption 5 is out now!

BestCrypt Volume Encryption is a comprehensive and practical program that provides transparent encryption of all the data stored in your disk devices, regardless of their type. It allows you to encrypt modern volumes, MS-DOS style disk partitions and various Windows 8 storage spaces.
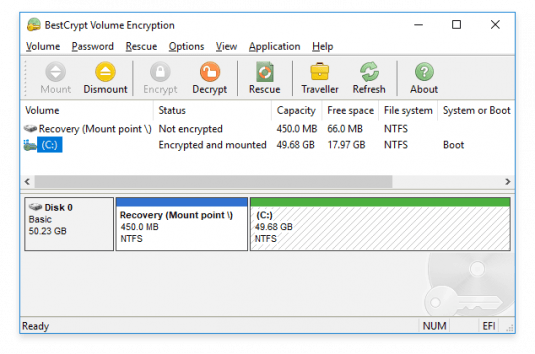
Once you launch the application, you will notice that all the available partitions are listed in the main window, no matter the type of file system they are, be it NTFS, FAT or FAT32. It encrypts each partition you want and allows you to get access to them without keeping in mind all the necessary aspects regarding the physical location of the volume.
For those who have worked with the ‘Disk Management’ feature (that each Windows operating system comes with), they will surely know how to work with this application since its main window is quite similar to the aforementioned utility, except for the menus. Basic details about each volume are also displayed, so you can easily view each one’s capacity, status, file system type, volume type and algorithm.
Moreover, as BestCrypt Volume Encryption allows you to encrypt data with strong algorithms, namely ‘AES (Rijndael)’, ‘RC6’, ‘Serpent’ and ‘Twofish’, you can rest assured that all your data is secured against unauthorized users.
When it comes to encrypting the selected volume, you are able to choose the algorithm you are interested in, select the format mode, then specify the password that will protect your entire volume. In case you don’t complete the encryption procedure, the application will notify you at a predefined period of time.
Another important function of BestCrypt Volume Encryption is that it allows you to manage passwords for encrypted volumes in several ways. In case you want to insert a new password, simply choose the volume you are interested in, then run the ‘Add Password’ command, from the Volume menu.
BestCrypt Volume Encryption Features
BestCrypt Volume Encryption Features
1. BestCrypt software is specially designed for Windows (32-bit and 64-bit operating systems). The software meets all the requirements of 32-bit and 64-bit software and uses all the available advantages of the operating system.
2. There is no limit on the number of local physical drives that users store BestCrypt containers. Any type of physical media can be used to store and access data on BestCrypt containers: hard drives, moveable media, magneto-optical devices, etc.
3. BestCrypt software can use any network accessible disc to create and access file containers. The network disk can be shared by servers with any operating system, such as UNIX-like operating systems (OSF / 1, LINUX, BSD, SunOS, HP / UX, AIX, etc.), Novell, Windows.
4. Users can copy (back up) BestCrypt containers from one computer to another and continue to access encrypted data without any restrictions of operating system type. For example, users can copy or move file containers from computers with Windows operating systems to UNIX computers, and then continue to access data from Windows computers (now stored in containers on UNIX computers).
5. The main command to control access to encrypted data can run from Windows Explorer (“My Computer” window) without starting the BestCrypt control panel. To run these commands from Explorer, you should use the same method as creating and opening any other documents from Explorer, such as Microsoft Word documents.
To sum things up, BestCrypt Volume Encryption enables you to encrypt any volume you want with ease, so all your data will stay protects against unauthorized access. Also, you are able to boot encrypted volumes only from a trusted network.

Apart from Jetico, what is the other method of endpoint protection?
About ATech Communication (HK) Limited
ATech Communication (HK) Ltd is one of the leading IT equipment & service provides for HKSAR Government Departments and Bureaux. We provide the best value and the best IT solution to our customers. Please visit our Cases page to learn more about our successful works. For more information on ATech, please contact us at enquiry@atechcom.net.
Jetico EndPoint Protection FAQ
When an attack crosses all your prevention work and hijacks your network and data, it is easy for you to pay ransom. When you compare the payment costs of employees who are unable to work and lose business due to future reputation damage during the downtime, the average ransom requirement paid seems to be economical. However, companies that pay ransoms do not receive decryption keys, and in many cases, companies are repeatedly attacked. So please don't pay ransom to those lawbreakers.
Jetico released BestCrypt Data Shelter, a new cybersecurity tool that’s integrated with all Jetico encryption products. Designed to protect files and folders even when they’re in use, Data Shelter builds on the data-at-rest capabilities of BestCrypt products and provides customers with an additional layer of security. BestCrypt Data Shelter is also available independently as freeware.
- Protect selected folders from unwanted programs and users
- Create protection policies for any number of folders
- Keep track of your encrypted drives and receive reminders about non-encrypted volumes
BestCrypt Volume Encryption is a comprehensive and practical program that provides transparent encryption of all the data stored in your disk devices, regardless of their type. It allows you to encrypt modern volumes, MS-DOS style disk partitions and various Windows 8 storage spaces.
1. BestCrypt software is specially designed for Windows (32-bit and 64-bit operating systems). The software meets all the requirements of 32-bit and 64-bit software and uses all the available advantages of the operating system.
2. There is no limit on the number of local physical drives that users store BestCrypt containers. Any type of physical media can be used to store and access data on BestCrypt containers: hard drives, moveable media, magneto-optical devices, etc.
3. BestCrypt software can use any network accessable disc to create and access file containers. The network disk can be shared by servers with any operating system, such as UNIX-like operating systems (OSF / 1, LINUX, BSD, SunOS, HP / UX, AIX, etc.), Novell, Windows.
4. Users can copy (back up) BestCrypt containers from one computer to another and continue to access encrypted data without any restrictions of operating system type. For example, users can copy or move file containers from computers with Windows operating systems to UNIX computers, and then continue to access data from Windows computers (now stored in containers on UNIX computers).
5. The main command to control access to encrypted data can run from Windows Explorer ("My Computer" window) without starting the BestCrypt control panel. To run these commands from Explorer, you should use the same method as creating and opening any other documents from Explorer, such as Microsoft Word documents.

ATech Communication (HK) Limited
Providing a Complete Suite of IT Solutions
- (852) 2970 6010 / 3756 0078
- enquiry@atechcom.net


